RID Hijacking: Maintaining access on Windows machines
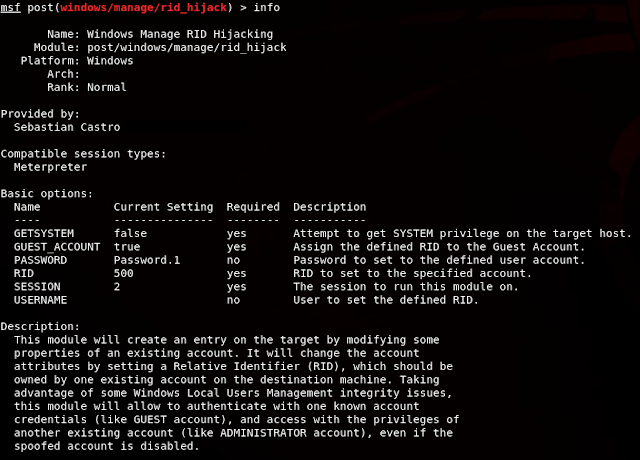
Read the full academic paper at ACM CCS CheckMATE 24 - Ghost in the SAM: Stealthy, Robust, and Privileged Persistence through Invisible Accounts Check my new website r4wsec.com The art of persistence is ( and will be... ) a matter of concern when successfully exploitation is achieved. Sometimes is pretty tricky to maintain access on certain environments, specially when it is not possible to execute common vectors like creating or adding users to privileged groups, dumping credentials or hashes, deploying a persistent <bind/reverse> shell, or anything that could trigger an alert on the victim. This statement ratifies why it's necessary to use discrete and stealthy techniques to keep an open door right after obtaining a high privilege access on the target. What could be more convenient that only use OS resources in order to persist an access? This is the new post-exploitation technique which I have named RID Hijacking . The RID Hijacking Attack By using only OS r...